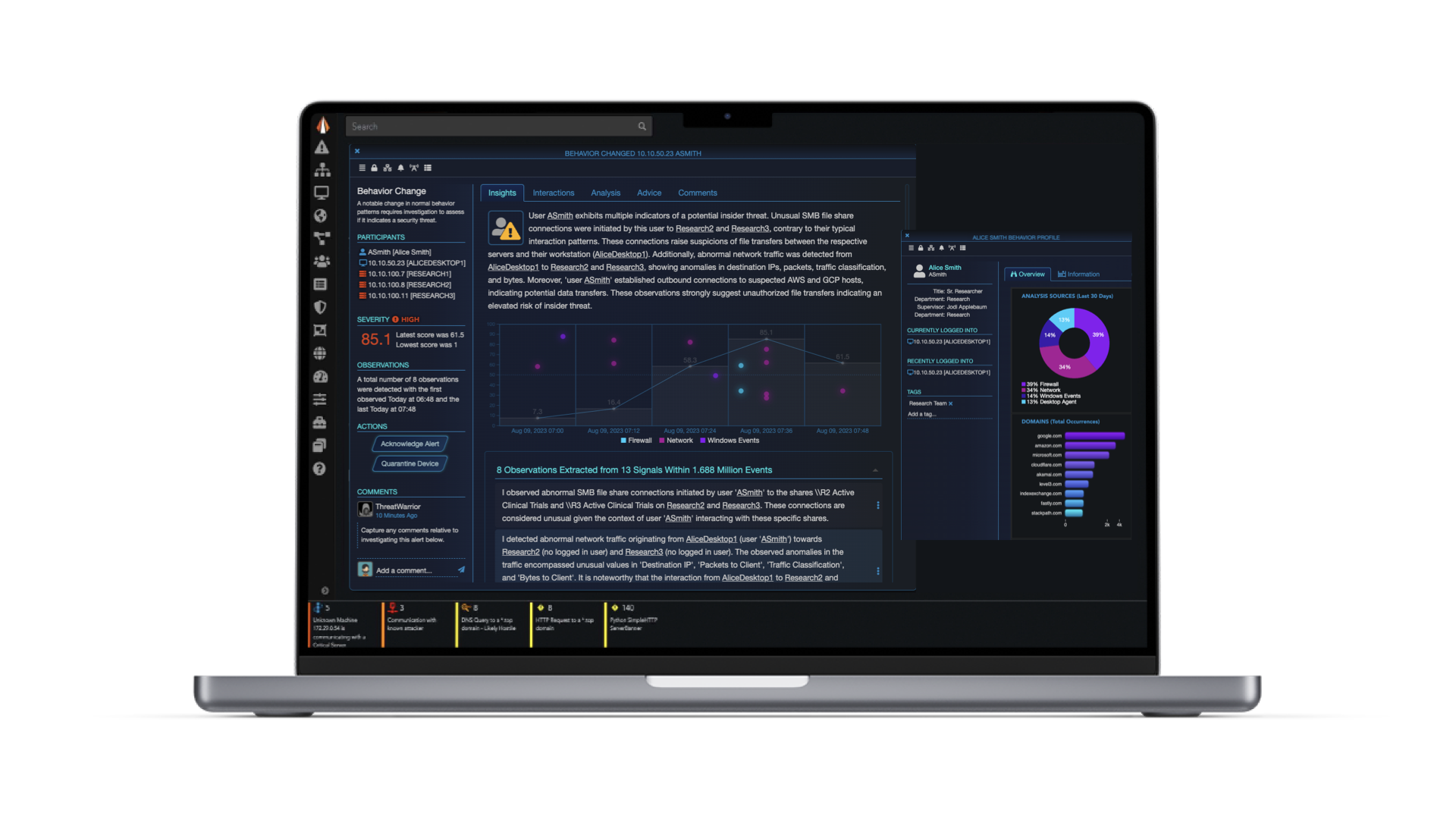
The ThreatWarrior Advantage
At ThreatWarrior, we do one thing really well. We convert your network, endpoint, and identity data into clear threat detection and response decision-making.
Our threat detection and response platform is the best ally your security team will ever have.

We scour the right data
for you.
On-premises, cloud, hybrid, network, endpoint, identity — everything. All collected, normalized, and ready for analysis.
We analyze the data
for you.
Everything is correlated, contextualized, prioritized, and visualized — performed by unsupervised neural networks and deep learning.

We translate all analyses
for you.
Natural Language Processing creates a simple narrative that makes it fast and easy to move to response and remediation action.
ThreatWarrior Roots out the
Most Dangerous Business Threats
Your security prevention layer is not enough. Attackers will get in. ThreatWarrior NDR and XDR solutions add the detection and response layer needed to address mid-business to mid-enterprise security challenges.

Digital Supply Chain Attacks
Software supply chain attacks could exceed $46B in 2023.
How ThreatWarrior helps:
- Monitors the entire digital supply chain, swiftly identifying suspicious activities and potential threats
- Provides a holistic view of the supply chain, enabling proactive risk mitigation and response strategies
- Intelligent automation facilitates rapid incident containment and minimizes attack impact
Insider Threats
2/3 of insider threats come from negligence.
How ThreatWarrior helps:
- Monitors user behavior to detect unusual file access or data exfil attempts
- Identifies unauthorized access to sensitive info or attempts to bypass security controls
- Analyzes network, endpoint and identity signals for signs of unauthorized system access or privilege escalation

Operational Technology (OT) Threats
McKinsey estimates the damage per OT attack at $140 million per incident.
How ThreatWarrior helps:
- Employs unsupervised neutral networking algorithms to detect unusual network behavior / patterns
- Continuously monitor network traffic for signs of data exfil or unauthorized access
- Analyze syslogs and network events to identify potential incidents
The Real Key is what ThreatWarrior
Does to Help Security Teams
Traditional defense-in-depth approaches and a wish for more human capital will not stem the tide. Organizations must leverage advanced AI.
ThreatWarrior’s unsupervised neural networks, continuous deep packet inspection, and Contextual Insights™ hold the keys. Learn how ThreatWarrior helps security teams move from ‘puzzle solvers’ to ThreatWarriors.





Start where you choose. Expand as you need.
Our AI-advanced threat detection and response platform can serve as an NDR or XDR solution. The difference lies only in the data sources you choose.
Prefer to run purely on network data sources like netflow and/or firewall logs?
Go with our NDR solution.
Want to enrich threat detection abilities with endpoint and identity data?
Go with our XDR solution.
It’s that simple. We don’t get caught up in acronyms, and you shouldn’t either.
We’ll always argue the network is the ground truth, but our unsupervised neural networking only gets smarter as you give it more data.
Explore more from ThreatWarrior
VIDEO
Prioritize alerts with Intelligent Threat Scoring
BLOG
Why do you need digital supply chain protection?
JOIN THE TEAM
Help us create a world where the good guys win
Take Back the Power
ThreatWarrior is shifting the power back to the defenders by helping security teams detect and stop attacks before they become breaches – keeping you far ahead of threat actors.
Get a one-on-one demo with a ThreatWarrior security expert to see how.