Unprecedented Visibility. Continuous Protection.
Network Detection & Response
ThreatWarrior safeguards your hybrid enterprise and keeps you immune from cyberattacks. Gain insight, visibility and real-time protection across your entire digital estate.
See Everything
Packets don’t lie. NDR analyzes packet data in network traffic (on-premises, cloud, or hybrid) to detect potential cyber threats.
Learn Behaviors
Learn the behavior of everything communicating on your network through our proprietary approach to deep learning.
Act Efficiently
Act efficiently to learn about and stop cyber threats, streamlining triage, investigation, response and remediation.
Prioritize alerts and reduce noise with ThreatWarrior NDR
ThreatWarrior’s hybrid approach to NDR security unifies many different network defense engines into a single platform. Each of those engines provides a score that ThreatWarrior unifies and integrates with threat intelligence reports from the cybersecurity community — harmonizing scoring consistently and pragmatically across the board.
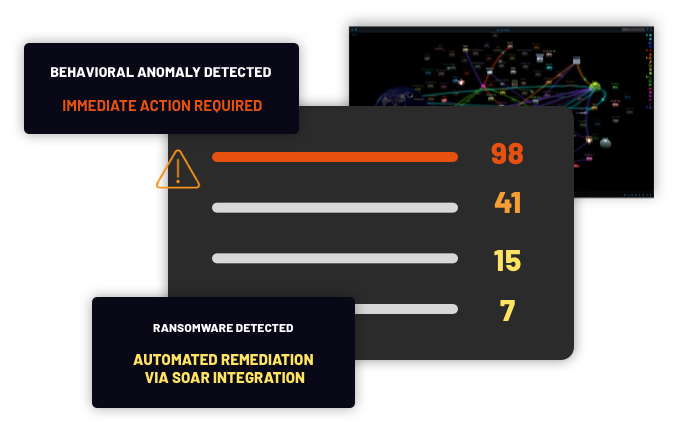
Define and govern policies to triage low-level threats
Extend compliance and policy enforcement across your enterprise with ThreatWarrior. While endpoint detection and response (EDR) protects devices such as servers and desktop computers, our network detection and response (NDR) platform helps protects your networks by identifying security gaps and vulnerabilities, defining policies, and automating their enforcement, making corporate governance easier.
We correlate network context with entity behavior to identify and respond to policy violations immediately. Configure ThreatWarrior to suspend network access for suspect devices, initiate triage and remediation workflows for compliance infractions, and alert your security team if further action is needed.
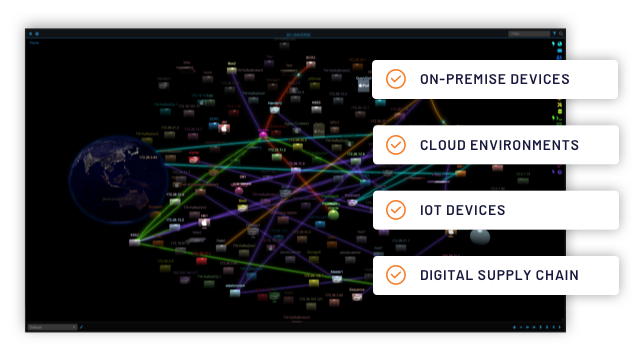
See everything on your network with the 3D Universe
ThreatWarrior’s 3D Universe provides complete, unified visibility into your enterprise ecosystem: on-premises devices, cloud environments, IoT, everything.
The graphical interface is simple and intuitive and shows all connected entities and data flow in real-time. The 3D Universe exposes anomalous activity and emerging threats while prioritizing the most critical issues to keep your team focused where needed.
Our visual explanation of security incidents and their context provides meaningful information for all users, from security operations (SecOps) to chief information security officers (CISOs).
How does NDR work?
Deploy anywhere
Deploy on-premises, private or public cloud, or hybrid environments with easy integration into your network and existing security tools.
Immediate results
ThreatWarrior network detection and response immediately begin to protect your network without complex configurations or agent installation.
Continuous learning
After turning on your sensors, ThreatWarrior starts to understand normal and abnormal behaviors for your environment to prioritize threats.
Contextual Intelligence Across Every Infrastructure to Deliver Signal
Digital Supply Chain Protection
Protect your critical applications, systems, cloud workloads, and digital supply chain relationships across your entire ecosystem.
Network Detection and Response
Protect your infrastructure and devices, whether managed or unmanaged, on-premises or in the cloud with next-generation NDR.