NLP in Cybersecurity: A Force Multiplier
In the evolving landscape of cybersecurity, new and sophisticated threats are constantly arising. To stay one step ahead, security teams are turning to advanced tools and techniques. One of the most promising technologies leading the charge is Natural Language Processing (NLP). Deployed correctly, NLP in cybersecurity is not just a fancy tool – it’s the automated management ‘context builder’ that saves loads of valuable time in response and remediation.

What is Natural Language Processing (NLP)?
Before we dive into how NLP aids in cybersecurity, it’s important to understand what NLP is. In a nutshell, Natural Language Processing gives machines the ability to understand, interpret, and respond to human language. This can include tasks like sentiment analysis, translation, or text summaries.
Imagine your digital assistant – it uses NLP to respond to your voice commands, translating your words into actions. Similarly, when used in cybersecurity, NLP can turn a chaotic stream of cyber threat alerts into intelligent, actionable items.
How Can NLP Help Security Teams?
NLP in cyber security is multi-faceted and expanding. It helps security teams on many fronts including threat intelligence gathering, alert triage, phishing detection and user behavior analysis. While ThreatWarrior leverages NLP on multiple fronts, there is one that deserves a special drill-down: Incident Response Automation.
By understanding natural language, NLP can assist in automating responses to simple or recurring security incidents, reducing workload and response time.
Even after automating alert correlation, contextualization and triage, a security team can still face hundreds to thousands of alerts each day. It can be hard for analysts of any experience level to understand complex situations with many sub-alerts and events.
Consider an example:
In Scenario 1, a security investigation is underway. It looks to be serious and needs quick attention. But the remediation could have consequences for a high-level employee, busy department, or revenue-producing function.
Corrective action may require executive approval. You present the following findings to your chain of command:

While technically accurate, this content still requires careful reading, attention and digestion. Your management is certainly capable given enough time. But they will be too busy, too impatient, or perhaps not knowledgeable enough to understand fully what they are reading.
You will need to find a more succinct explanation. This is not only annoying and time consuming for you, it also extends Mean-Time-To-Respond (MTTR).
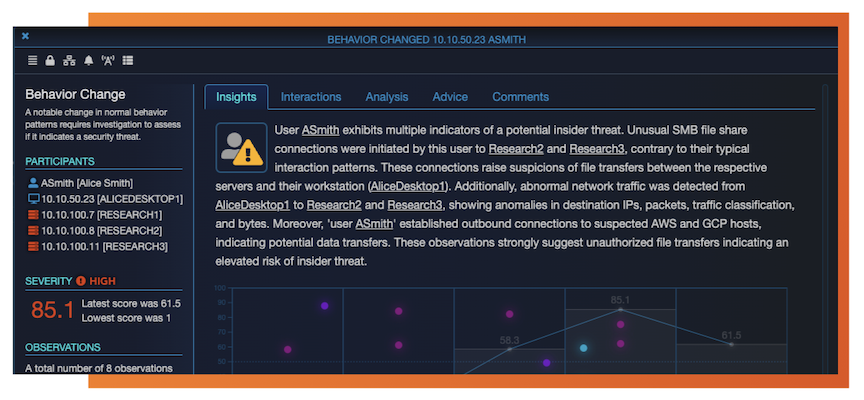
In Scenario 2, we convert the alert string into a narrative that anyone can easily understand – in real time. The screenshot to the right is an actual NLP-generated narrative from within ThreatWarrior.
Arcane data is transformed into actionable intelligence. This reduces work for the security team, and improves management’s understanding of an alert. Further, it speeds the remediation approval process, ultimately reducing business risk.
The Power of Extended Detection and Response (XDR) in NLP in Cybersecurity
ThreatWarrior’s Extended Detection and Response (XDR) system leverages NLP applications across the following use cases:

ThreatWarrior XDR converts technical data to fast-action executive communication.
Data analysis is core to threat detection and response, but fast understanding across decision-makers is as vital. NLP helps reduce mean time to respond by simplifying technical discovery.

ThreatWarrior XDR provides speeds up the learning curve for less experienced analysts.
Piecing together arcane alerts and events into action is not easy. Tier 3 analysts and threat hunters can decipher “code speak” fast. Less experienced analysts need more time and guidance.
ThreatWarrior XDR parses threat feeds into accurate context around emerging threats.
Threat feed are the essential security ‘weather reports’. These feeds are unique in their data sharing and format. NLP is excellent at normalizing feeds for both human and decision engine processing.
Security teams cannot scale quickly enough, let alone affordably. The pressure to find attacker activity, process it, and communicate it so other stakeholders can understand it will also only increase. For these reasons, machine learning, language modeling and NLP will only grow in importance over the coming years. A strong XDR solution equipped with NLP will help your cybersecurity team to stay one step ahead of the hackers.