Proactive Cyber Resilience: Enhancing Operational Technology (OT) Security
Information Technology (IT) has been, without question, the lifeblood of most modern organizations for decades now. IT systems and tools underpin every business process, empowering employees to deliver increasing value with less time, energy and cost.
But IT is not the only lifeblood for many businesses. OT connects, monitors, manages, and secures every industrial organization’s operations. Businesses including manufacturing, mining, oil and gas, utilities, transportation, and many others, rely heavily on OT. OT includes robots, ICS, SCADA, PLCs, and CNC – all used for system control and automation.
Additionally, OT is not only prevalent in factories. ATMs, information kiosks, connected buses, trains, weather stations, and electric vehicle charging stations are all examples of sprawling OT networks.
As you might expect, if a cyberattack brings down OT, it is not a nuisance. It instantly affects our lives.
OT Security Use Cases
To underscore the significance of OT security, let’s consider a few use cases:
 In manufacturing, implementing OT security solutions can prevent unauthorized access, detect anomalies, and enable real-time threat response, minimizing disruptions.
In manufacturing, implementing OT security solutions can prevent unauthorized access, detect anomalies, and enable real-time threat response, minimizing disruptions.
 In the energy sector, a strong OT security plan can protect power grids from cyberattacks.
In the energy sector, a strong OT security plan can protect power grids from cyberattacks.
![]()
In public transportation, effective OT security can prevent train collisions.
OT security plays a critical role in today’s digital transformation journey. IT and OT interconnectivity will only increase. At the same time, cyber criminals see OT systems as goldmines for ransomware payouts.
IT vs. OT Security
OT security challenges are unique. Unlike traditional IT systems, OT networks operate
real-time systems that directly impact physical safety. Here are some key points of differentiation:
IT devices are profiled as follows:
- Typically off-the-shelf
- Lifespan of three to five years
- Relatively easy to maintain
- Run on generalized operating systems like Windows, iOS, and Linux
- Focus on data access, processing, and human decision-making
- Protects data from unauthorized access
OT devices are different on a number of dimensions:
- Tend to be purpose-built
- Often run by specialized software and proprietary protocols
- All about availability and safety
- Prevents disruptions to physical processes
A cyberattack on OT systems can lead to physical damage, service disruption, and even endanger lives.
For example, if someone halts robots, manufacturing production stops. If someone hacks a SCADA system, they can dump sewage into water reservoirs (it has happened).
This brings us to the crucial difference between IT and OT security. Traditionally, IT and OT have operated separately, often in silos. However, due to the rise of OT-targeted cyber threats, this approach is rapidly changing.
As these systems converge, security teams must consider the unique security requirements of each domain.
Tools for OT Security Monitoring
You need OT security monitoring tools to address these challenges. The efficacy of a security analyst depends on their tool chain. Staying ahead of sophisticated threat actors necessitates employing advanced monitoring tools that offer real-time visibility into OT environments.
OT security monitoring tools play a critical role in detecting abnormal behaviors, identifying vulnerabilities, and enabling quick response to threats. They provide features such as asset discovery, network monitoring, anomaly detection, and incident response, empowering organizations to safeguard their critical infrastructures.
Nevertheless, the implementation of these tools should not occur in isolation. A comprehensive approach to security, one that integrates OT and IT, proves most effective in protecting both digital and physical assets.
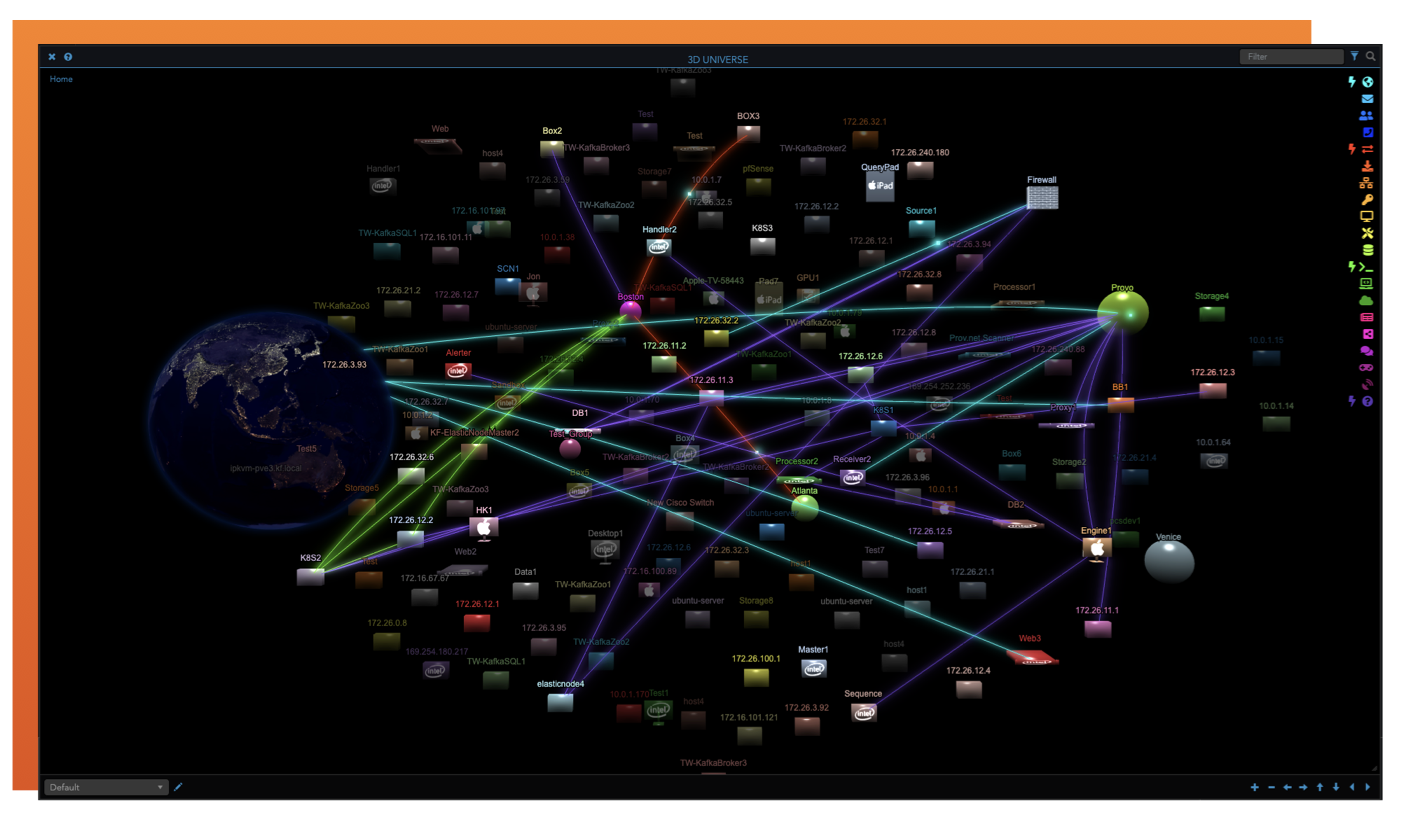
Empowering OT Security with ThreatWarrior Extended Detection and Response (XDR)
Extended Detection and Response (XDR) is an emerging technology that makes significant strides in mitigating OT threats. ThreatWarrior XDR provides organizations with one system to detect and respond to threats across an organization’s IT and OT infrastructure:
Real-time Visibility
ThreatWarrior XDR provides real-time visibility into IT and OT networks, enabling early threat detection and response to potential security incidents. Visibility extends beyond traditional perimeter security measures into IT and OT devices, user behavior, and network traffic.
Data Correlation
ThreatWarrior XDR collects and correlates data across disparate security products – critical for OT environments where the stakes are high. By identifying easily missed threats in real-time, ThreatWarrior XDR ensures operational continuity and safety.
Real AI
ThreatWarrior XDR’s unsupervised neural networking and continuous deep packet inspection capabilities do the tough work of prioritizing and contextualizing alerts. This frees security teams to focus precious time and energy on response and mitigation.
Cyber threats to OT environments are on the rise. ThreatWarrior XDR tips the scales back in favor of security teams through cutting-edge detection and response.