THREATWARRIOR OT
Complete OT Protection
Gain 100% visibility across your OT environments. Protect against known and unknown threats, strengthen operational resilience, and detect threats that other solutions miss.
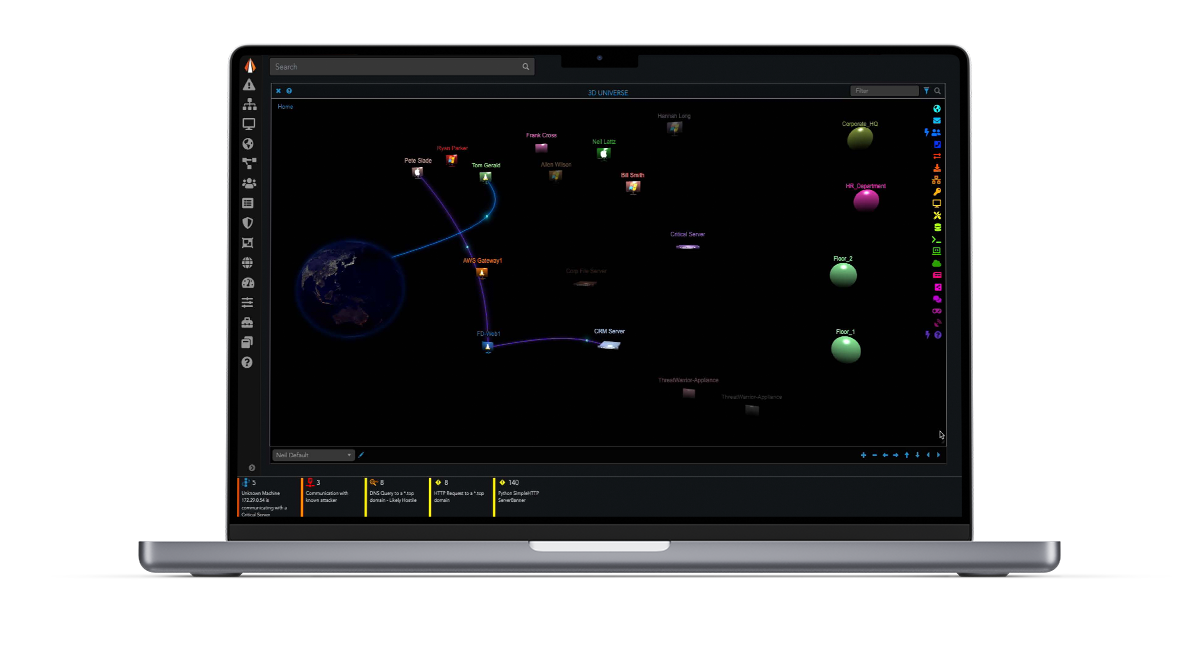
Complete Visibility
Discover threats and early indicators of compromise across OT, legacy systems, ICS, SCADA, and much more.

Agentless
ThreatWarrior is passive and agentless, so we are invisible to threat actors, cannot be turned off or evaded, and protect OT that cannot support endpoint agents.
Network Truth
We use continuous deep packet inspection to examine network traffic in real time to find the ground truth of what’s happening across your IT and OT environments.
Continuous Threat Protection
ThreatWarrior OT empowers you to immediately detect and respond to threats across your industrial environment. Our platform is always monitoring for known and unknown threats to help you stop attacks before they impact operations.

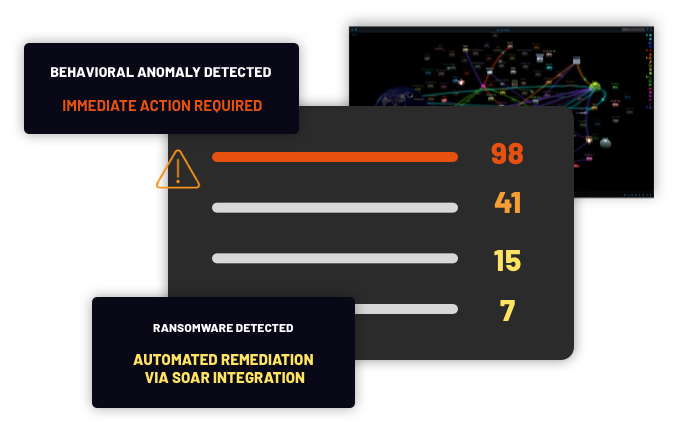
Constantly-Evolving AI
ThreatWarrior uses deep unsupervised neural networks to self-learn what is normal for your OT environments — and what isn’t. We help identify and stop threats at the earliest stages, even for legacy technology that can’t keep up with emerging threats.
Always-Up-to-Date Asset Inventory
You can’t protect what you can’t see. ThreatWarrior OT delivers a constantly updated asset inventory to comprehensively manage all assets in your industrial operations. Detect when new devices access your environment, and protect technology that cannot support other security approaches like endpoint agents.
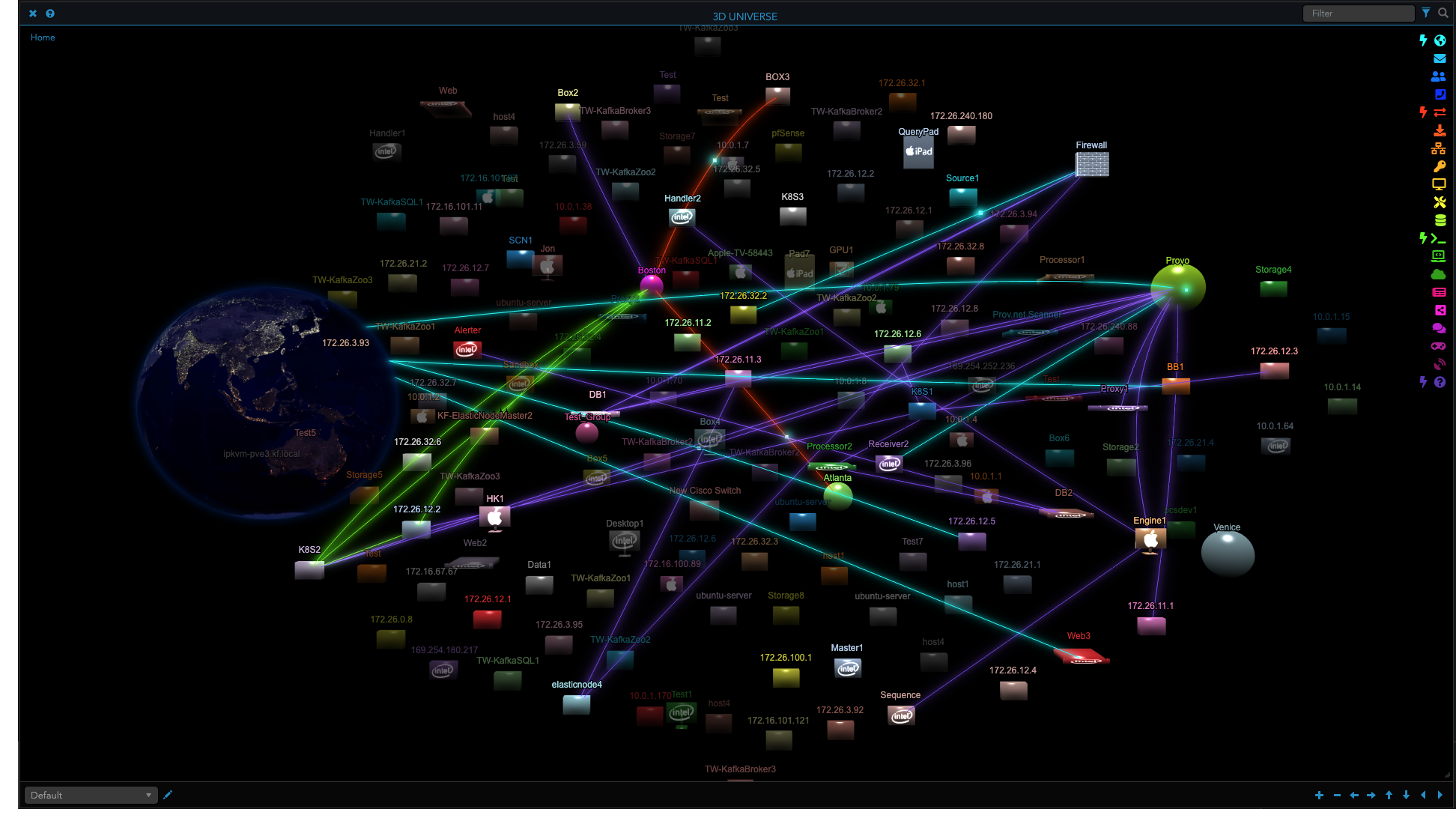
UNIFIED OT SECURITY
ThreatWarrior’s multiple engines work together to analyze and correlate data, adding contextual intelligence to alerts. This helps reduce false positives and filter out low-risk threats, keeping your team focused on the most consequential threats to your complex OT and hybrid IT/OT environments.
Behavioral Engine
Unsupervised neural networks self-learn the normal operating behavior of all entities on your network, alerting you and autonomously responding when anomalies are detected. This approach is significantly more accurate and sophisticated than other AI and machine learning techniques.
Insights Engine
Rules and Policies Engine
Deep Packet Inspection Engine
Integrations Engine
Cloud Entity Detection Engine
Get a Demo
Schedule your demo with a ThreatWarrior security expert to learn how we can help you see everything happening on your network and detect active threats to your OT environments.