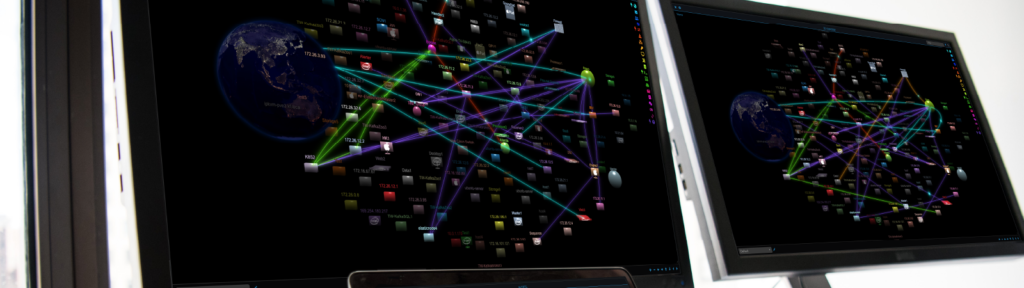
The advanced technology, ThreatWarrior™ , applies artificial intelligence modeled after the human immune system that learns and adapts to internal and external threats facing organizations.
ThreatWarrior, a leading provider of machine-learning technology, today announced the availability of ThreatWarrior™, a next-generation cyber defense solution that applies unsupervised deep neural networks to cyber threat and behavior monitoring.
ThreatWarrior™ integrates with an organization’s network and, without interruption to existing information systems, passively observes all network traffic. It utilizes artificial intelligence, machine learning and unsupervised deep neural networks to observe data, learn behaviors and predict potential cyberattacks. ThreatWarrior™ provides analysis of detected threats by self-learning the network of people and devices, including IoT and industrial controls systems (ICS), to determine what is ‘normal’ behavior – providing a Cyber Immune Response™ modeled after the human immune response when anomalies are detected. ThreatWarrior™ detects indicators of zero-day exploits, malware, ransomware, phishing, malicious insider activity and other cyber threats in real time across physical, virtual and cloud-based networks.
“Our population’s dependence on complex technology continues to grow and, at the same time, the threat environment continues to grow and evolve in a uniquely dynamic and daunting way,” said Pete Slade, ThreatWarrior’s CTO. “We realized traditional approaches for cybersecurity that focus inward on understanding and addressing vulnerabilities, weaknesses, and configurations, while necessary, are insufficient to detect rapidly evolving internal or external threats.”
Concerned by this growing cyber threat, and feeling an obligation to contribute to a solution, ThreatWarrior began focusing efforts toward applying its machine learning and behavioral analysis experience to cyber defense. After sharing an early prototype, ThreatWarrior was encouraged to commercialize ThreatWarrior™ by members of the intelligence community.
“The ability to persist and cause ongoing damage is motivating the need to move beyond today’s traditional reactive, perimeter-based approaches to cybersecurity,” Slade continued. “We believe that artificial intelligence driven computer network defense offers a more resilient security posture for ever-expanding, ever-evolving threats. This method even allows for detection of zero-day attacks, and other generally unknown activities through which systems are compromised using techniques yet to be discovered and patched by vendors.”
ThreatWarrior™ employs a unique combination of engines that work in tandem to maximize threat detection efficacy: an intelligence engine, an unsupervised deep neural network AI, a compliance engine, and an integrity engine.
ThreatWarrior™ is an appliance-based solution, installed behind the user’s firewall at the core switch. This enables the system to passively analyze all observed data, while providing maximum security as sensitive data never has to leave the organization’s premises. ThreatWarrior™ is available in different appliance sizes to facilitate small to large and distributed deployments, ensuring that all organizations have the same protection opportunity. Solution highlights include:
Solution highlights include:
Detection: Identifies threats in real time, including malware activities, botnets, zero-day attacks, behavior anomalies, external attackers, compliance violations, insiders and advanced persistent threats (APT).
- 3D Threat Visualizer: Designed on top of WebGL using video game engine paradigms for an easy-to-use immersive 3D experience, ThreatWarrior™ provides global oversight, situational awareness, real-time threat alerts, rewind and replay of activity, along with notifications and analytics.
- Data Capture: Performs deep packet inspection on network traffic and logs for all networks and devices – physical, virtual and cloud. Captures switch traffic, syslog, metadata, raw PCAP info and more.
- Immediate Value: ThreatWarrior™ provides immediate value, detecting threats on day one while continuously learning and adapting to the user’s environment.
- Intuitive Searches: Easily search for and analyze data, protocols, events and network traffic with ThreatWarrior™. Point-in-time history retention allows users to examine past events.
Because it consolidates and analyzes data in real time, the solution delivers immediate proactive insights. Additionally, it is capable of integrating with surveillance solutions such as facial and speech recognition systems to optimize any security environment.
About ThreatWarrior
ThreatWarrior, the cyber awareness platform for threat hunting and mitigation, empowers organizations to seek out and neutralize cyber threats. ThreatWarrior self-learns and adapts to an always-changing threat landscape. It vigilantly guards against cyber attacks—even ones that don’t exist yet. For more information, visit threatwarrior.com.