What is Continuous Deep Packet Inspection?
Continuous deep packet inspection (DPI) is a powerful technique for inspecting and filtering network traffic. DPI evaluates the packet header and contents in order to identify malware and classify traffic by application protocols.
Unlike traditional packet capture and plain packet filtering, continuous DPI examines more than just packet headers and can understand the sessions that connect packets together. It allows you to dissect and analyze the packet payload and all network data, identifying granular information from end to end. Continuous deep packet inspection enhances network security by helping you understand which application packets belong to, and by revealing network patterns and user behavior — and it provides this information 24/7 in real time.
Why is Continuous Deep Packet Inspection Important?
Continuous deep packet inspection significantly enhances enterprise security and a user’s understanding of the network. By fully parsing and inspecting the entire application payload of a packet and reassembling traffic sessions, continuous DPI enables security teams to detect more dangerous and complex attacks by correlating heuristics and behavioral-based analytics.
Continuous DPI also helps monitor traffic and identify what is running on the network. This allows organizations to enforce rules that prevent confidential information from leaving the network or alert when unsupported software is detected.
Additionally, millions more IoT devices continue to come online every year, and most aren’t built with security-by-design principles. There are no inherent security standards to prevent them from being hacked. Continuous DPI helps security teams understand more about IoT security flaws, and can help prevent IoT DDoS and botnet attacks.
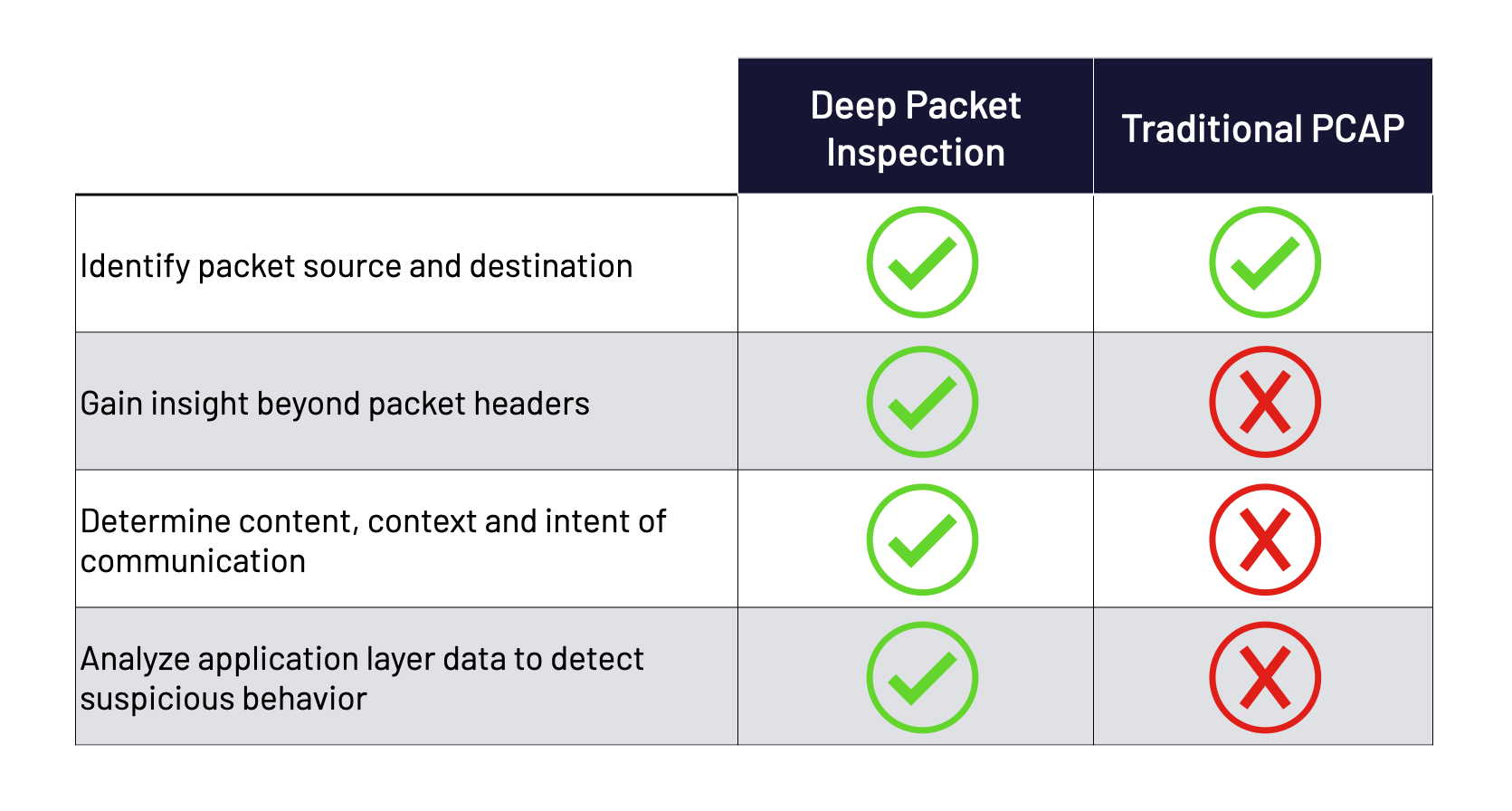
Continuous Deep Packet Inspection vs. Traditional Packet Capture
Without utilizing continuous deep packet inspection, cybersecurity solutions cannot constantly extract or filter any information beyond packet headers without costly full packet capture. The packet header merely provides basic information like the sender and receiver and the time the packet was sent. This is used to generate net flows that track traffic patterns between two devices.
Net flows allow IT teams to see rough metrics of network traffic, helping determine its source, destination, and volume—and not much else. But it’s all that some antiquated security solutions can see to monitor a network.
Consider telephone logs as an analogy for net flows. These call logs show you that someone is calling into your organization, how long they talked, and how their call was routed, but provide no information beyond that.
Call logs cannot take into account the content or context of a conversation, and therefore it is impossible to determine the intent of the call. Is the caller phoning in a threat to the organization, attempting a socially engineered phishing attempt, or innocently attempting to make a payment? Is the caller contacting the sales department but having a conversation completely unrelated to sales activity?
Continuous deep packet inspection allows you to answer these questions. It enables advanced network monitoring, data analysis and filtering, and next-generation network protection. With constantly evolving threats increasing in volume and velocity, continuous DPI is a critical aspect of a comprehensive network security strategy.
How ThreatWarrior uses Continuous DPI
ThreatWarrior goes beyond traditional PCAP, performing continuous deep packet inspection on data in motion, even in the cloud. We enable clients to see everything connected to their network, including all devices and cloud workloads as part of our network detection and response solution.
Our Continuous Deep Packet Inspection Engine performs traffic discovery with more than 6 million traffic classifications and 250 protocols. Our solution observes actual network traffic, leapfrogging first-generation solutions that trust well-known ports to determine traffic type. ThreatWarrior performs signature detection in-flight on more than 30,000 known threat signatures, so it can identify all threats across the wire including the many manifestations of malware, trojans, and advanced persistent threats.
We allow users to know what’s inside the wire, reassembling all packets and inspecting every byte in real time to detect attack signatures. Our continuous DPI, including protocol detection and traffic classification, begins immediately upon deployment without complex configurations, delivering immediate value to your team. Plus, our data collection is passive so there is no disruption to your business.
ThreatWarrior’s use of continuous DPI delivers visibility into layers 2 through 7 of the Open Systems Interconnection (OSI) model, which means we allow our clients to see everything from the data layer (2) all the way to the application layer (7). While many first-generation solutions don’t analyze L7 traffic, ThreatWarrior does this in real time which enables our clients to identify suspicious behavior and mitigate threats that are obscured at lower layers of the network stack, greatly enhancing enterprise security.
Because ThreatWarrior captures such an extensive amount of data, we ensure it is not accessible outside of the sensor or the user’s organization. Even we don’t have access to the data, keeping your confidential information where it should be – in your hands only.
Contact ThreatWarrior today and request a demo to learn more.



