Many enterprises today are built on a hybrid or multi-cloud architecture, and the rising demand for cybersecurity solutions that can protect these cloud infrastructures has grown exponentially. However, some vendors still focus security efforts only on certain platforms. Unfortunately, that approach leaves organizations with partial security and open to cyberattacks.
Organizations leveraging cloud infrastructure like Google Cloud’s powerful suite of infrastructure and applications require new approaches to cybersecurity. ThreatWarrior offers just that.
Our partnership with Google Cloud allows us to leverage Google’s infrastructure in unique ways for the benefit of our customers. Our AI platform protects organizations’ hybrid and Google Cloud deployments, enabling businesses to drastically improve cloud security.
So how do we do it? First, a look at ThreatWarrior.
What is ThreatWarrior?
ThreatWarrior is a next-generation network threat intelligence platform that utilizes a unique blend of sophisticated engines to provide businesses with the ability to see everything, learn from that complete visibility and then take action to remediate potential risks.
A key design principle for ThreatWarrior is the ability to provide network threat intelligence no matter the infrastructure of a customer’s environment. Our platform enables security teams to detect anomalies, suspicious behavior, and policy violations across hybrid and multi-cloud networks.
ThreatWarrior utilizes multiple engines that work together to calculate a Threat Score which provides an easy-to-understand look at your threat landscape. The Threat Score is dynamic and extensible, so that as your network evolves, ThreatWarrior learns and adapts to these changes, adjusting to your ‘new normal’ to ensure Threat Score accuracy over time.
The ThreatWarrior architecture is comprised of two major components:
- Virtual sensors, which passively and continuously analyze network traffic to provide full transparency into what is on or interacting with the company network.
- The “core,” which is where unsupervised neural networks process data to identify patterns that represent a threat to an organization.
The virtual sensors leverage deep packet inspection to provide real-time cybersecurity protection and feed the core with information about network traffic so the AI engine can provide intelligence on potential threats or bad actors that have infiltrated the network.
Gain Complete Visibility
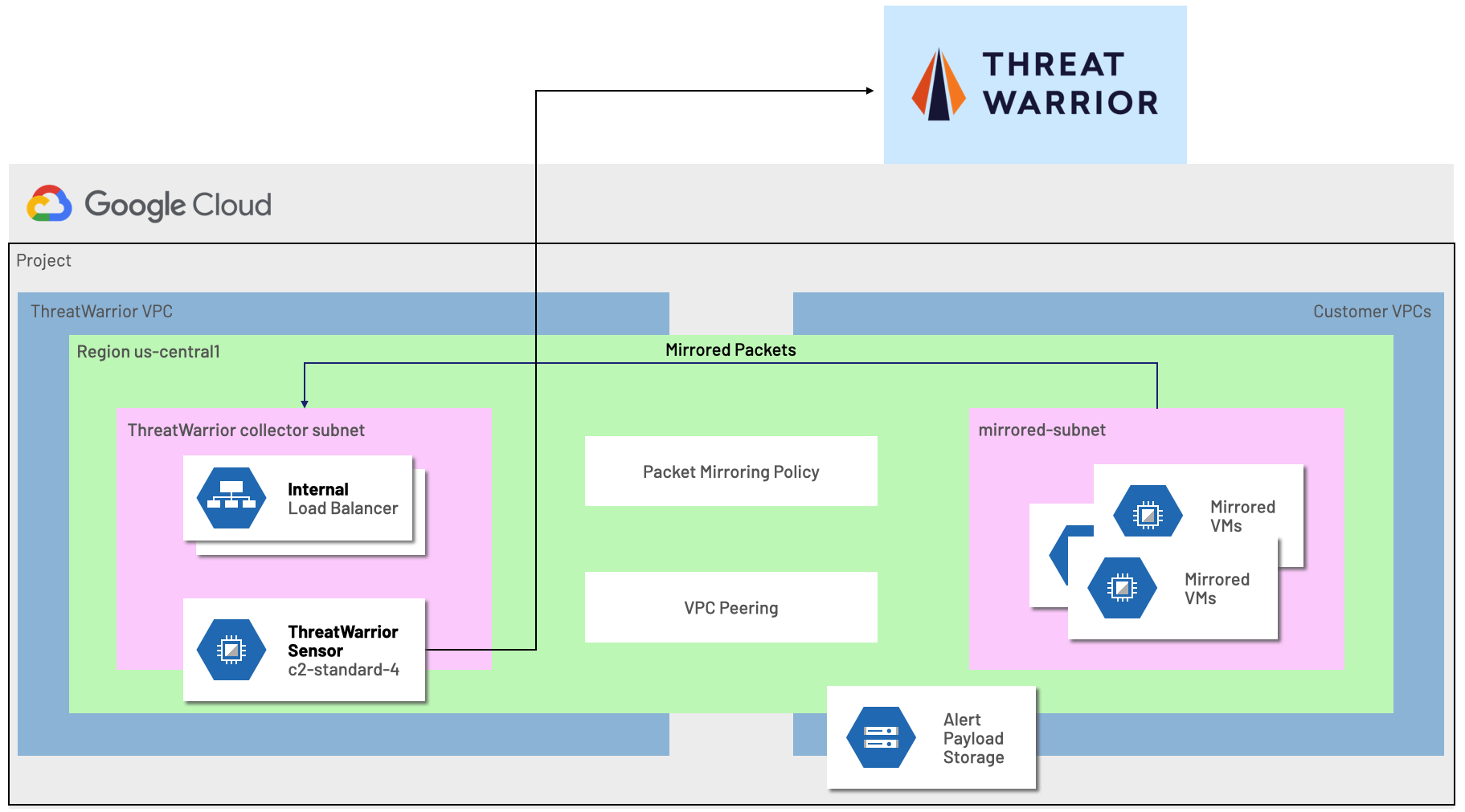
ThreatWarrior performs continuous deep packet inspection to analyze cloud workloads, leveraging the availability of Packet Mirroring within a Google Cloud VPC. An agentless ThreatWarrior virtual sensor is deployed within your environment observing the network traffic and communication patterns of your networked devices.
ThreatWarrior automatically classifies, tracks, and maps dependencies between all entities. The platform gives security teams complete visibility into all communication over the network, including east-west and cloud communication. This visibility is critical to prevent breaches.
ThreatWarrior performs protocol detection to understand what is moving over network ports, checks for known-signatures of malware, ransomware, and suspicious behavior and learns the behavioral patterns of connected devices. Additionally, ThreatWarrior ensures that observed packet data never leaves your environment (maintaining your chain of custody).
Google Cloud and ThreatWarrior Integration
ThreatWarrior’s core consists of both a Network Security Platform and a Behavioral Learning Platform, both of which leverage Google Cloud. ThreatWarrior selected Google Cloud as the infrastructure for its next-generation platform due to the strength of Google’s Kubernetes implementation, GPU accessibility and quality of the development experience.
Our integration with Google Cloud Platform Packet Mirroring helps customers identify compromised instances, detect threats such as lateral movement, and respond to cyber threats — all at the speed and scale of the cloud.
Contact ThreatWarrior today for more information, or schedule a demoto see how you can now leverage ThreatWarrior for fully native network threat detection and response within Google Cloud – giving you peace of mind that you have full visibility and defense for your cloud-based assets.



