GROUP PRODUCT MANAGER
NETWORK SECURITY AT GOOGLE CLOUD
Monitors and inspects cloud traffic at scale with packet mirroring
Automatically discovers and profiles Google Cloud workloads without installing agents
Provides complete visibility into cloud workloads, virtual machines, compute instances and containers
Continuously monitors and classifies cloud entities with deep packet inspection
Enables proactive threat hunting, rapid detection, response and investigation across multiple environments
Uses deep learning AI to determine true malicious intent, eliminating noise and alert fatigue
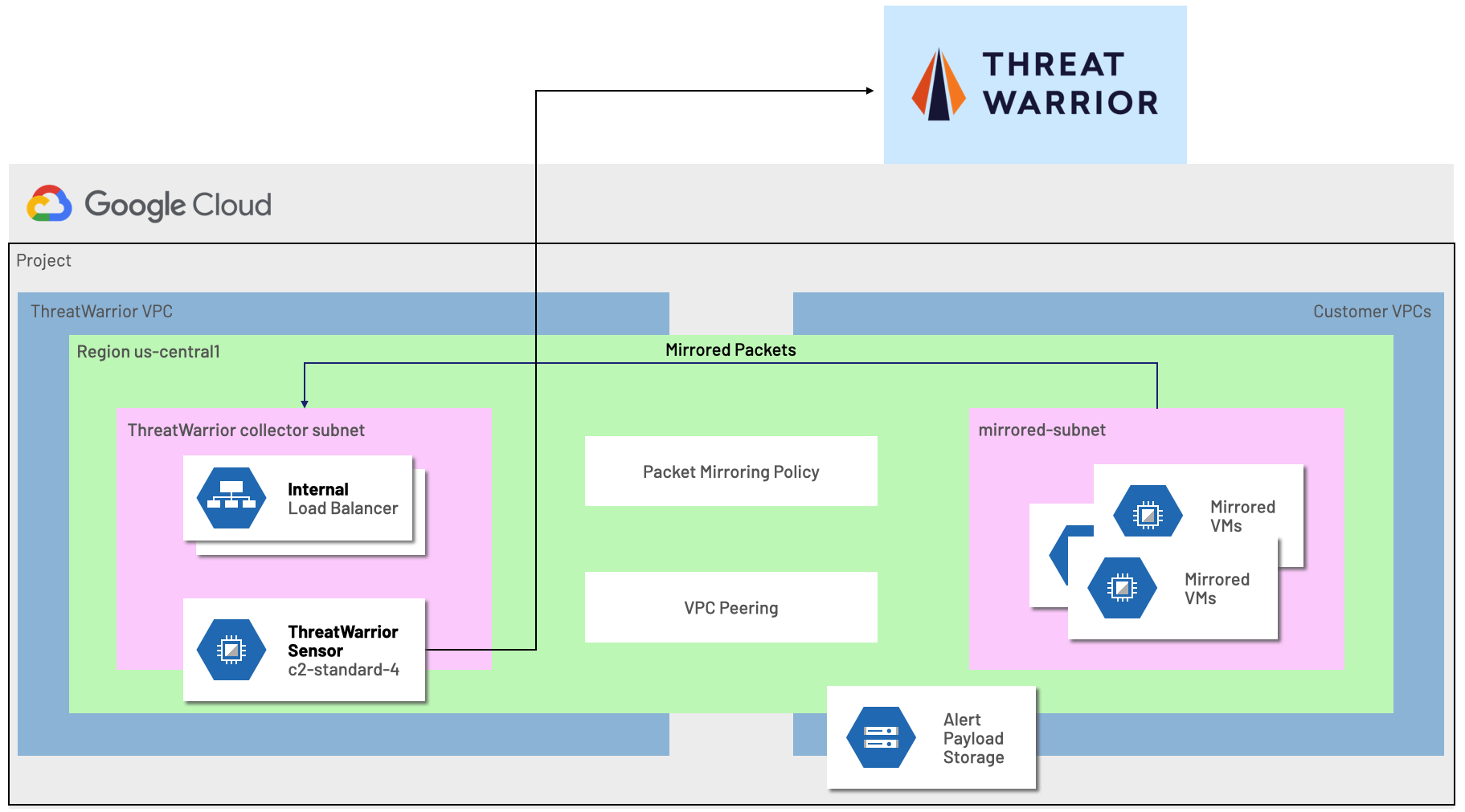
ThreatWarrior performs continuous deep packet inspection to analyze cloud workloads, leveraging the availability of Packet Mirroring within a Google Cloud VPC. An agentless ThreatWarrior virtual sensor is deployed within your environment observing the network traffic and communication patterns of your networked devices.
ThreatWarrior automatically classifies, tracks, and maps dependencies between all entities. The platform gives security teams complete visibility into all communication over the network, including east-west and cloud communication. This visibility is critical to prevent breaches.
ThreatWarrior performs protocol detection to understand what is moving over network ports, checks for known-signatures of malware, ransomware, and suspicious behavior and learns the behavioral patterns of connected devices. Additionally, ThreatWarrior ensures that observed packet data never leaves your environment, maintaining your chain of custody.

Enhance Cybersecurity by Leveraging Google Packet Mirroring in ThreatWarrior
Many enterprises today are built on a hybrid or multi-cloud architecture, and the rising demand for cybersecurity solutions that can protect these cloud infrastructures has grown exponentially. However, some vendors still focus security efforts only on certain platforms. Unfortunately, that approach leaves organizations with partial security and open to cyberattacks.
Organizations leveraging cloud infrastructure like Google Cloud’s powerful suite of infrastructure and applications require new approaches to cybersecurity. ThreatWarrior offers just that.


