Ransomware is growing at an alarming rate — up 150% in 2020 and spiking even higher in 2021, with more than half of infected businesses paying the ransom. (1) The list of high-profile ransomware attacks grows almost daily, affecting government agencies, critical infrastructure, health organizations, schools, and more.
In the wake of these continued cybersecurity catastrophes, President Biden recently issued an Executive Order aimed and improving the nation’s cybersecurity. (2) Additionally, given the rise in volume, velocity, and maliciousness of criminal ransomware, the U.S. Department of Justice is elevating the investigation of ransomware attacks to a similar priority as terrorism. (3)
Cybersecurity professionals have been warning about an explosion in the number of high-profile ransomware attacks for years, with the public and private sectors at large not heading their warnings.
It’s time for that to change.
Stop Ransomware Attacks with ThreatWarrior
While not necessarily as sophisticated as some attacks organizations face today, ransomware poses a serious and growing threat. This form of malware encrypts a victim’s files and the group responsible demands a ransom payment before restoring the victim’s access to its data. Some also threaten to release a victim’s private data if they are not paid off, a situation the Washington D.C. police department is currently enduring.(4)
Ransomware attacks in general are easy for ThreatWarrior to detect, as there are many opportunities for anomaly detection across the Tactics, Techniques, and Procedures (TTPs) involved in the crime. And because these attacks are carried out by criminals, not nation-state actors, they use well known, off-the-shelf Command and Control (C2) tools to coordinate their probes, and they rely primarily on tried-and-true known vulnerabilities instead of zero-day attacks.
After ransomware gangs find a way past perimeter security, they have to move laterally until they gain a foothold where they can escalate privileges. Then, they have to fan out over the network to find valuable data. With data in hand, they have to exfiltrate the pristine, readable copy for blackmail. Finally, they pull the trigger to encrypt the data for ransom. At each step, there are ways for ThreatWarrior’s multiple engines to detect the incursion.
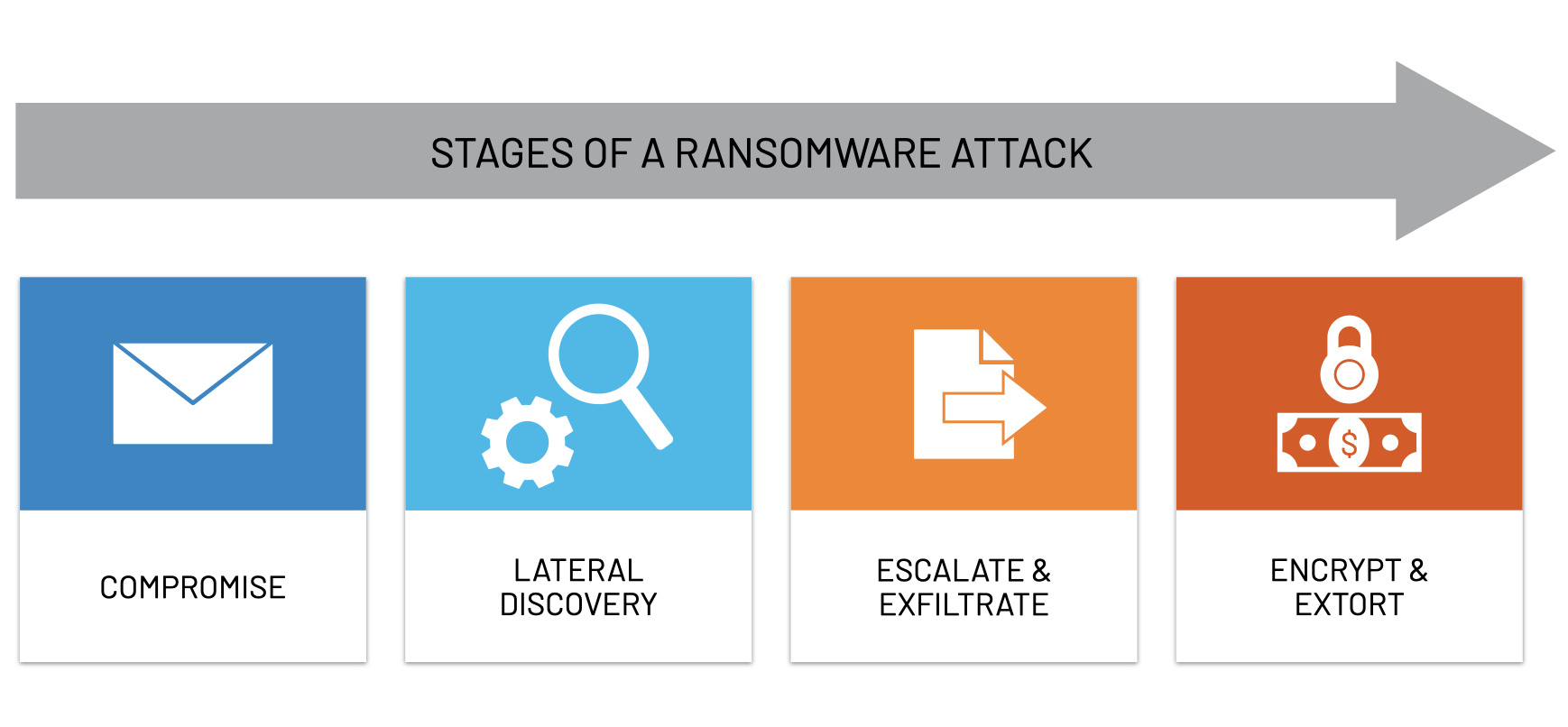
- Threat actors using ransomware must enter the perimeter somewhere, and many organizations still rely on signature-based detection and perimeter defense. This leaves them completely vulnerable once an attack is already inside. ThreatWarrior delivers complete visibility across your entire digital estate. Once bad actors are inside, ThreatWarrior would see unusual external communication from C2 agents on impacted devices, as well as have opportunities to perform deep packet inspection and match that traffic against signatures of C2 systems known to the threat intel community. Put simply, ThreatWarrior would quickly identify any suspicious activity that looked like ransomware, whether known or unknown.
- Privilege escalation provides even more opportunities for ThreatWarrior to detect anomalous traffic and match packets against known vulnerabilities.
- Once ransomware gangs control the ground, the reconnaissance stage involves many unusual connections between devices on the network as well as IP scans, offering even more opportunities for anomaly detection.
- Data exfiltration involves large volumes of data being sent to external IPs from devices which do not usually do that, creating yet more opportunities for anomaly detection.
- Finally, when encryption is triggered, there is a flurry of activity as the command is sent to all the compromised devices. ThreatWarrior would find and alert to this anomalous activity from a ransomware attack.
All of these opportunities are missed if no one’s looking. That’s why the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, (5) along with the Multi-State Information Sharing & Analysis Center, (6) urge all organizations to follow best practices to prevent ransomware:
- “Detect command and control activity and other potentially malicious network activity that occurs prior to ransomware deployment.”
- “Baseline and analyze network activity over a period of months to determine behavioral patterns so that normal, legitimate activity can be more easily distinguished from anomalous network activity.”
ThreatWarrior not only excels at both of these best practices — they are core capabilities of the platform.
_______
It is only a matter of time before another attack like this happens. If the SolarWinds and Colonial Pipeline attacks or other major hacks haven’t woken you up yet, it’s time. Organizations must step up to the plate and put cybersecurity at the forefront, or risk suffering the same fate.

Your organization can stop ransomware attacks with network detection and response solutions. Learn what is network detection and response how we can help and, as always, stay vigilant.
References:
1) https://hbr.org/2021/05/ransomware-attacks-are-spiking-is-your-company-prepared
2) https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/
3) https://www.reuters.com/technology/exclusive-us-give-ransomware-hacks-similar-priority-terrorism-official-says-2021-06-03/
4) https://www.washingtonpost.com/local/public-safety/dc-police-hackers-ransomware-babuk/2021/05/13/d0280fb4-b3f7-11eb-a980-a60af976ed44_story.html
5) https://www.cisa.gov/
6) https://www.cisecurity.org/ms-isac
7) https://www.cnet.com/news/privacy/solarwinds-hackers-accessed-dhs-acting-secretarys-emails-what-you-need-to-know/
8)



